使用kubeasz安装k8s集群 1 节点规划 因机器配置比较低所以采用精简配置,所有节点均为2c2g
角色
数量
描述
etcd节点
1
注意etcd集群需要1,3,5,…奇数个节点,一般复用master节点
master节点
1
高可用集群至少2个master节点
node节点
2
运行应用负载的节点,可根据需要提升机器配置/增加节点数
生产环境可以参考
类型
备注
ansible * 2
k8s集群部署服务器,可以和其他服务器混用
k8s master * 3
k8s控制端,通过一个vip做主备做高可用
harbor * 2
高可用镜像服务器
etcd * 3
保存k8s集群数据的服务器
haproxy * 2
高可用etcd代理服务器
node节点 * (2 - N)
真正运行容器的服务器端,高可用环境至少两台
2 Linux Kenel升级 k8s,docker,cilium等很多功能、特性需要较新的linux内核支持,所以有必要在集群部署前对内核进行升级;CentOS7 和 Ubuntu16.04可以很方便的完成内核升级。
CentOS7
红帽企业版 Linux 仓库网站 https://www.elrepo.org,主要提供各种硬件驱动(显卡、网卡、声卡等)和内核升级相关资源;兼容 CentOS7 内核升级。如下按照网站提示载入elrepo公钥及最新elrepo版本,然后按步骤升级内核(以安装长期支持版本 kernel-lt 为例)
rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.orgrpm -Uvh http://www.elrepo.org/elrepo-release-7 .0 -3 .el7.elrepo.noarch.rpmyum --disablerepo=\* --enablerepo=elrepo-kernel repolistyum --disablerepo=\* --enablerepo=elrepo-kernel list kernel*yum --disablerepo=\* --enablerepo=elrepo-kernel install -y kernel-lt.x86_64yum remove kernel-tools-libs.x86_64 kernel-tools.x86_64 -yyum --disablerepo=\* --enablerepo=elrepo-kernel install -y kernel-lt-tools.x86_64awk -F\' '$1 =="menuentry " {print $2 }' /etc/grub2.cfg CentOS Linux (4 .4 .183 -1 .el7.elrepo.x86_64) 7 (Core) CentOS Linux (3 .10 .0 -327 .10 .1 .el7.x86_64) 7 (Core) CentOS Linux (0 -rescue-c52097a1078c403da03b8eddeac5080b) 7 (Core)grub2 -set-default 0
Centos 7.9 查询到的第一个内核是拯救模式内核,所以应该选1作为默认启动项,注意不要选错了
[root@node-1 ~]# awk -F' ‘$1==”menuentry “ {print $2}’ /etc/grub2.cfg
3 基础环境准备 安装python
yum update python python -y
部署节点安装ansible
curl -O https ://bootstrap .pypa .io /pip /2 .7 /get-pip.py python get-pip.py python -m pip install --upgrade "pip < 21.0" pip install ansible -i https ://mirrors .aliyun .com /pypi /simple /
在ansible控制端配置免密码登录
'' -f ~/.ssh/i d_ed255192048 -N '' -f ~/.ssh/i d_rsa$IPs $IPs ln -s /usr/ bin/python3 /u sr/bin/ python
附:
分发公钥脚本
# !/bin/bash # 目标主机列表
同步docker证书脚本
同步docker证书脚本# !/bin/bash # 目标主机列表
4 部署节点编排k8s安装 3.0 .0 //gi thub.com/easzlab/ kubeasz/releases/ download/${release}/ ezdown
[root@master kubeasz]# ./ezdown -D % Total % Received % Xferd Average Speed Time Time Time Current
上述脚本运行成功后,所有文件(kubeasz代码、二进制、离线镜像)均已整理好放入目录/etc/kubeasz
[root@master kubeasz] 14 months ago 350MB 15 months ago 473MB 16 months ago 373MB 16 months ago 226MB 17 months ago 121MB 18 months ago 34.5MB 18 months ago 57.2MB 19 months ago 42.4MB 19 months ago 262MB 19 months ago 22.8MB 19 months ago 110MB 19 months ago 52.9MB 2 years ago 683kB 2 years ago 39.9MB 1 root root 10284 2月 1 2021 ansible.cfg 3 root root 4096 4月 25 17:02 bin 8 root root 92 2月 2 2021 docs 2 root root 4096 4月 25 17:08 down 2 root root 70 2月 2 2021 example 1 root root 22436 2月 1 2021 ezctl 1 root root 13660 2月 1 2021 ezdown 10 root root 145 2月 2 2021 manifests 2 root root 4096 2月 2 2021 pics 2 root root 4096 2月 2 2021 playbooks 1 root root 5640 2月 1 2021 README.md 22 root root 4096 2月 2 2021 roles 2 root root 48 2月 2 2021 tools
创建集群配置实例
ezctl new k8s-01
然后根据提示配置’/etc/kubeasz/clusters/k8s-01/hosts’ 和 ‘/etc/kubeasz/clusters/k8s-01/config.yml’:根据前面节点规划修改hosts 文件和其他集群层面的主要配置选项;其他集群组件等配置项可以在config.yml 文件中修改。
[root@manager kubeasz]# cat clusters/k8s-01/config.yml# # prepare # # 可选离线安装系统软件包 (offline|online) # 可选进行系统安全加固 github.com/dev-sec/ansible-collection-hardening # 设置时间源服务器【重要:集群内机器时间必须同步】 # 设置允许内部时间同步的网络段,比如"10.0.0.0/8" ,默认全部允许 # # role:deploy # # default: ca will expire in 100 years # default: certs issued by the ca will expire in 50 years # kubeconfig 配置参数 # # role:runtime [containerd,docker] # # ------------------------------------------- containerd # [.]启用容器仓库镜像 # [containerd]基础容器镜像 # [containerd]容器持久化存储目录 # ------------------------------------------- docker # [docker]容器存储目录 # [docker]开启Restful API # [docker]信任的HTTP仓库 # # role:kube-master # # k8s 集群 master 节点证书配置,可以添加多个ip和域名(比如增加公网ip和域名) # - "k8s.test.io" # - "www.test.com" # node 节点上 pod 网段掩码长度(决定每个节点最多能分配的pod ip地址) # 如果flannel 使用 --kube-subnet-mgr 参数,那么它将读取该设置为每个节点分配pod网段 # https://github.com/coreos/flannel/issues/847 # # role:kube-node # # Kubelet 根目录 # node节点最大pod 数 # 配置为kube组件(kubelet,kube-proxy,dockerd等)预留的资源量 # 数值设置详见templates/kubelet-config.yaml.j2 # k8s 官方不建议草率开启 system-reserved, 除非你基于长期监控,了解系统的资源占用状况; # 并且随着系统运行时间,需要适当增加资源预留,数值设置详见templates/kubelet-config.yaml.j2 # 系统预留设置基于 4c/8g 虚机,最小化安装系统服务,如果使用高性能物理机可以适当增加预留 # 另外,集群安装时候apiserver等资源占用会短时较大,建议至少预留1g内存 # haproxy balance mode # # role:network [flannel,calico,cilium,kube-ovn,kube-router] # # ------------------------------------------- flannel # [flannel]设置flannel 后端"host-gw" ,"vxlan" 等 # [flannel] flanneld_image: "quay.io/coreos/flannel:v0.10.0-amd64" # [flannel]离线镜像tar包 # ------------------------------------------- calico # [calico]设置 CALICO_IPV4POOL_IPIP=“off”,可以提高网络性能,条件限制详见 docs/setup/calico.md # [calico]设置 calico-node使用的host IP,bgp邻居通过该地址建立,可手工指定也可以自动发现 # [calico]设置calico 网络 backend: brid, vxlan, none # [calico]更新支持calico 版本: [v3.3.x] [v3.4.x] [v3.8.x] [v3.15.x] # [calico]calico 主版本 # [calico]离线镜像tar包 # ------------------------------------------- cilium # [cilium]CILIUM_ETCD_OPERATOR 创建的 etcd 集群节点数 1,3,5,7... # [cilium]镜像版本 # [cilium]离线镜像tar包 # ------------------------------------------- kube-ovn # [kube-ovn]选择 OVN DB and OVN Control Plane 节点,默认为第一个master节点 # [kube-ovn]离线镜像tar包 # ------------------------------------------- kube-router # [kube-router]公有云上存在限制,一般需要始终开启 ipinip;自有环境可以设置为 "subnet" # [kube-router]NetworkPolicy 支持开关 # [kube-router]kube-router 镜像版本 # [kube-router]kube-router 离线镜像tar包 # # role:cluster-addon # # coredns 自动安装 # 设置 local dns cache 地址 # metric server 自动安装 # dashboard 自动安装 # ingress 自动安装 # prometheus 自动安装 # # role:harbor # # harbor version,完整版本号
[root@manager k8s-01]# cat hosts# 'etcd' cluster should have odd member(s) (1,3,5,...)# master node(s) # work node(s) # [optional] harbor server, a private docker registry # 'NEW_INSTALL' : 'yes' to install a harbor server; 'no' to integrate with existed one# 'SELF_SIGNED_CERT' : 'no' you need put files of certificates named harbor.pem and harbor-key.pem in directory 'down' # 192.168.68.8 HARBOR_DOMAIN="harbor.yourdomain.com" NEW_INSTALL=no SELF_SIGNED_CERT=yes # [optional] loadbalance for accessing k8s from outside # 192.168.68.6 LB_ROLE=backup EX_APISERVER_VIP=192.168.68.250 EX_APISERVER_PORT=8443 # 192.168.68.7 LB_ROLE=master EX_APISERVER_VIP=192.168.68.250 EX_APISERVER_PORT=8443 # [optional] ntp server for the cluster # 192.168.68.1 # --------- Main Variables --------------- # Cluster container-runtime supported: docker, containerd # Network plugins supported: calico, flannel, kube-router, cilium, kube-ovn # Service proxy mode of kube-proxy: 'iptables' or 'ipvs' # K8S Service CIDR, not overlap with node(host) networking # Cluster CIDR (Pod CIDR), not overlap with node(host) networking # NodePort Range # Cluster DNS Domain # -------- Additional Variables (don't change the default value right now) --- # Binaries Directory # Deploy Directory (kubeasz workspace) # Directory for a specific cluster # CA and other components cert/key Directory
开始安装 如果你对集群安装流程不熟悉,请阅读项目首页 安装步骤 讲解后分步安装,并对 每步都进行验证
# 一键安装 # 或者分步安装,具体使用 ezctl help setup 查看分步安装帮助信息 # ezctl setup k8s-01 01 # ezctl setup k8s-01 02 # ezctl setup k8s-01 03 # ezctl setup k8s-01 04 # ezctl setup k8s-01 05 # ezctl setup k8s-01 06 # ezctl setup k8s-01 06
验证安装:
master上运行
[root@master ~]# kubectl get node
可以看到node-1,node-2, master 正在运行
创建pod用于测试:
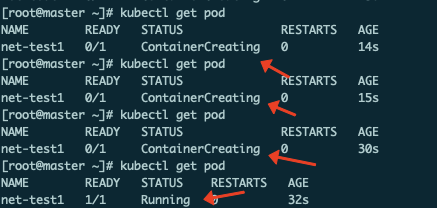
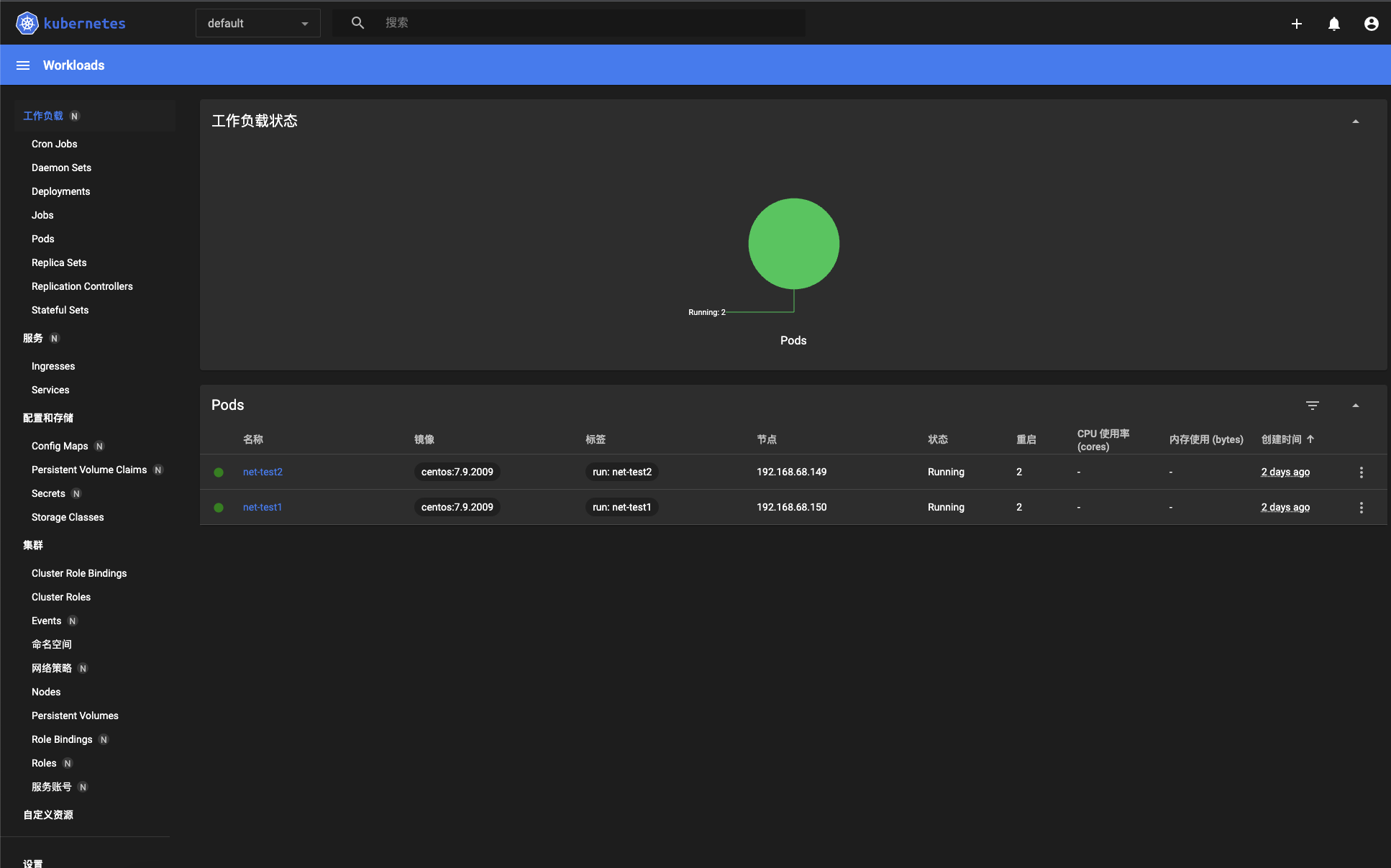
[root@master ~]# kubectl run net-test1 --image =centos:7.9.2009 sleep 36000
可以看到pod状态从ContainerCreating变成了Running,依法同样创建net-test2:
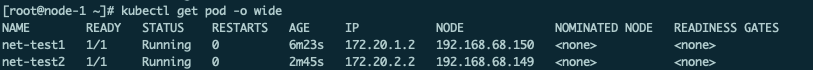
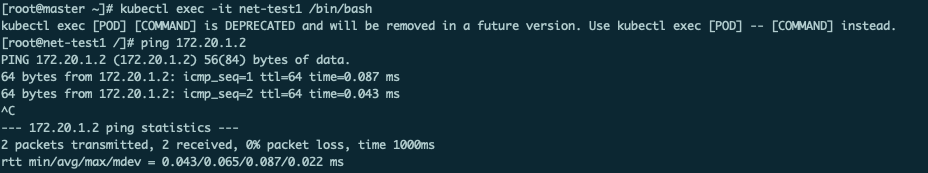
可以看到node1的ip:172.20.1.2, node2:172.20.2.2, 根据node信息,可以看到两个pod分别运行在两个node上,进入net-test1容器内部pingnet-test2,可以连通:
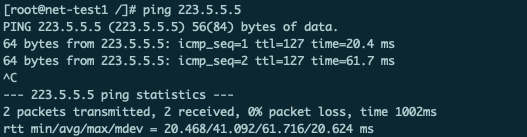
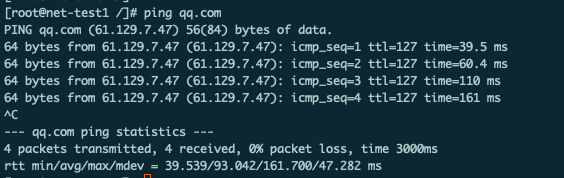
ping外网ip地址,可以连通:
此时ping外网域名是不通的,需要安装coreDNS用于解析域名
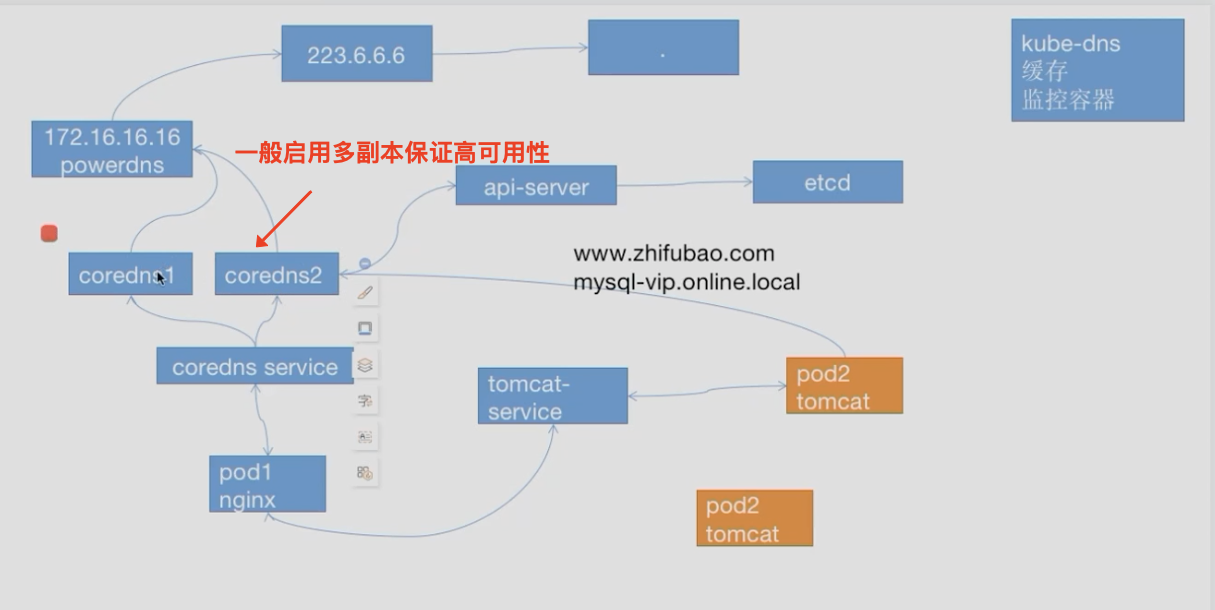
5 安装coreDNS 目前k8s主要使用coreDNS组件用于解析k8s集群中service name 所对应得到ip地址
相关文档: 官网
github: 地址
此处使用k8s的yaml文件方式安装,下载k8s软件包:https://dl.k8s.io/v1.23.5/kubernetes.tar.gz
下载完成后解压
进入kubernetes-1.23.5/cluster/addons/dns/coredns目录
可以看到coreDNS对应yaml文件,复制coredns.yaml.base为coredns.yaml打开
[root@manager coredns ]apiVersion: v1 kind: ServiceAccount metadata: name: coredns namespace: kube-system labels: kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: labels: kubernetes.io/bootstrapping: rbac-defaults addonmanager.kubernetes.io/mode: Reconcile name: system:coredns rules: - apiGroups: - "" resources: - endpoints - services - pods - namespaces verbs: - list - watch - apiGroups: - "" resources: - nodes verbs: - get - apiGroups: - discovery.k8s.io resources: - endpointslices verbs: - list - watch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: annotations: rbac.authorization.kubernetes.io/autoupdate: "true" labels: kubernetes.io/bootstrapping: rbac-defaults addonmanager.kubernetes.io/mode: EnsureExists name: system:coredns roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: system:coredns subjects: - kind: ServiceAccount name: coredns namespace: kube-system --- apiVersion: v1 kind: ConfigMap metadata: name: coredns namespace: kube-system labels: addonmanager.kubernetes.io/mode: EnsureExists data: Corefile: | .:53 { errors health { lameduck 5s } ready kubernetes magedu.local in-addr.arpa ip6.arpa { # 此处修改为和kubeasz中hosts文件一致 pods insecure fallthrough in-addr.arpa ip6.arpa ttl 30 } prometheus :9153 forward . /etc/resolv.conf { max_concurrent 1000 } cache 30 loop reload loadbalance } --- apiVersion: apps/v1 kind: Deployment metadata: name: coredns namespace: kube-system labels: k8s-app: kube-dns kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile kubernetes.io/name: "CoreDNS" spec: strategy: type: RollingUpdate rollingUpdate: maxUnavailable: 1 selector: matchLabels: k8s-app: kube-dns template: metadata: labels: k8s-app: kube-dns spec: securityContext: seccompProfile: type: RuntimeDefault priorityClassName: system-cluster-critical serviceAccountName: coredns affinity: podAntiAffinity: preferredDuringSchedulingIgnoredDuringExecution: - weight: 100 podAffinityTerm: labelSelector: matchExpressions: - key: k8s-app operator: In values: ["kube-dns" ]topologyKey: kubernetes.io/hostname tolerations: - key: "CriticalAddonsOnly" operator: "Exists" nodeSelector: kubernetes.io/os: linux containers: - name: coredns image: k8s.gcr.io/coredns/coredns:v1.8.6 imagePullPolicy: IfNotPresent resources: limits: memory: 200Mi requests: cpu: 100m memory: 70Mi args: [ "-conf" , "/etc/coredns/Corefile" ]volumeMounts: - name: config-volume mountPath: /etc/coredns readOnly: true ports: - containerPort: 53 name: dns protocol: UDP - containerPort: 53 name: dns-tcp protocol: TCP - containerPort: 9153 name: metrics protocol: TCP livenessProbe: httpGet: path: /health port: 8080 scheme: HTTP initialDelaySeconds: 60 timeoutSeconds: 5 successThreshold: 1 failureThreshold: 5 readinessProbe: httpGet: path: /ready port: 8181 scheme: HTTP securityContext: allowPrivilegeEscalation: false capabilities: add: - NET_BIND_SERVICE drop: - all readOnlyRootFilesystem: true dnsPolicy: Default volumes: - name: config-volume configMap: name: coredns items: - key: Corefile path: Corefile --- apiVersion: v1 kind: Service metadata: name: kube-dns namespace: kube-system annotations: prometheus.io/port: "9153" prometheus.io/scrape: "true" labels: k8s-app: kube-dns kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile kubernetes.io/name: "CoreDNS" spec: selector: k8s-app: kube-dns clusterIP: 10.68 .0 .2 ports: - name: dns port: 53 protocol: UDP - name: dns-tcp port: 53 protocol: TCP - name: metrics port: 9153 protocol: TCP
修改完成用使用kube apply命令创建对应容器
[root@master ~]# kubectl apply -f coredns.yaml
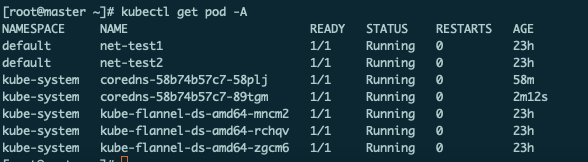
查看pod发现对应pod被创建:
[root@master ~]# kubectl get pod -A
再次在容器内部ping外网域名,此时外网域名可以正确解析
coreDNS 属于关键服务,宕机后整个集群域名无法解析,所以一般情况下会启用多个副本保证高可用:
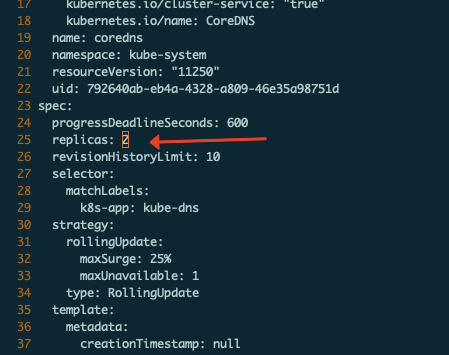
多副本coreDNS 最简单多部署方式就是修改对应yaml文件的replicas副本数定义,再重新kubectl apply使其生效,
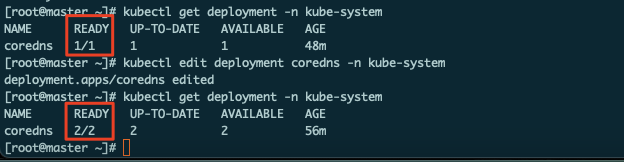
kubectl edit deployment coredns -n kube-system:
可以看到coreDNS副本数变为了2
yaml 部分参数解释 69 data: 70 Corefile: | 71 .:53 {72 errors 73 health {74 lameduck 5s 75 }76 ready 77 kubernetes magedu.local in-addr.arpa ip6.arpa {78 pods insecure 79 fallthrough in-addr.arpa ip6.arpa 80 ttl 30 81 }82 prometheus :9153 83 forward . /etc/resolv.conf {84 max_concurrent 1000 85 }86 cache 30 87 loop 88 reload 89 loadbalance 90 }
errors :错误记录到标准输出。
health :在 http://localhost:8080/health 处提供 CoreDNS 的健康报告。
ready :在端口 8181 上提供的一个 HTTP 末端,当所有能够 表达自身就绪的插件都已就绪时,在此末端返回 200 OK。
kubernetes :CoreDNS 将基于 Kubernetes 的服务和 Pod 的 IP 答复 DNS 查询。你可以在 CoreDNS 网站阅读更多细节 。 你可以使用 ttl 来定制响应的 TTL。默认值是 5 秒钟。TTL 的最小值可以是 0 秒钟, 最大值为 3600 秒。将 TTL 设置为 0 可以禁止对 DNS 记录进行缓存。
pods insecure 选项是为了与 kube-dns 向后兼容。你可以使用 pods verified 选项,该选项使得 仅在相同名称空间中存在具有匹配 IP 的 Pod 时才返回 A 记录。如果你不使用 Pod 记录,则可以使用 pods disabled 选项。
forward : 不在 Kubernetes 集群域内的任何查询都将转发到 预定义的解析器 (/etc/resolv.conf).
cache :启用前端缓存。
loop :检测到简单的转发环,如果发现死循环,则中止 CoreDNS 进程。
reload :允许自动重新加载已更改的 Corefile。 编辑 ConfigMap 配置后,请等待两分钟,以使更改生效。
loadbalance :这是一个轮转式 DNS 负载均衡器, 它在应答中随机分配 A、AAAA 和 MX 记录的顺序。
你可以通过修改 ConfigMap 来更改默认的 CoreDNS 行为, 参考 。
你可以追加本地权威DNS服务器,当本地有类似内网环境的特殊域名coreDNS无法解析的时候,可以把请求转发到本地权威DNS, 在上述配置后追加:
myserver.online { 172.16 .16 .16 :53 # 本地DNS的ip地址,例如bind9 }
6 安装Dashboard 使用官网提供的yaml文件安装,参考:https://github.com/kubernetes/dashboard/releases
Apply 方式安装后查看相关状态:
[root@master ~]# kubectl get pod -A -o wide1 /1 Running 2 2 d20h 172.20 .1.8 192.168 .68.150 <none> <none> 1 /1 Running 2 2 d20h 172.20 .2.8 192.168 .68.149 <none> <none> system coredns-58 b74b57c7-kv4lw 1 /1 Running 2 121 m 172.20 .1.9 192.168 .68.150 <none> <none> system kube-flannel-ds -amd64-mncm2 1 /1 Running 1 2 d20h 192.168 .68.152 192.168 .68.152 <none> <none> system kube-flannel-ds -amd64-rchqv 1 /1 Running 2 2 d20h 192.168 .68.150 192.168 .68.150 <none> <none> system kube-flannel-ds -amd64-zgcm6 1 /1 Running 2 2 d20h 192.168 .68.149 192.168 .68.149 <none> <none> 5 b8896d7fc-2 frf2 1 /1 Running 0 107 s 172.20 .1.10 192.168 .68.150 <none> <none> 897 c7599f-tvscb 1 /1 Running 0 107 s 172.20 .2.9 192.168 .68.149 <none> <none> get svc -A10.68 .0.1 <none> 443 /TCP 2 d21hsystem kube-dns ClusterIP 10.68 .0.2 <none> 53 /UDP,53 /TCP,9153 /TCP 46 h10.68 .203.30 <none> 8000 /TCP 3 m56s10.68 .183.139 <none> 443 /TCP 3 m57s
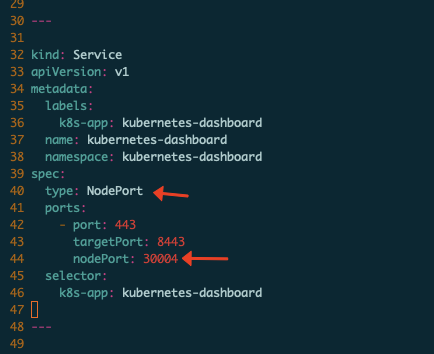
可以看到dashboard容器监听443端口,但并未对外暴露端口,需要修改yaml文件将端口暴露出来以便用户访问,打开yaml文件定位到如下位置:
增加type: NodePort, 增加nodePort: 30004,将端口暴露到物理机30004端口,此时查看svc
[root@master ~]
端口已经暴露,此时使用任意node ip:30004即可在浏览器打开dashboard: